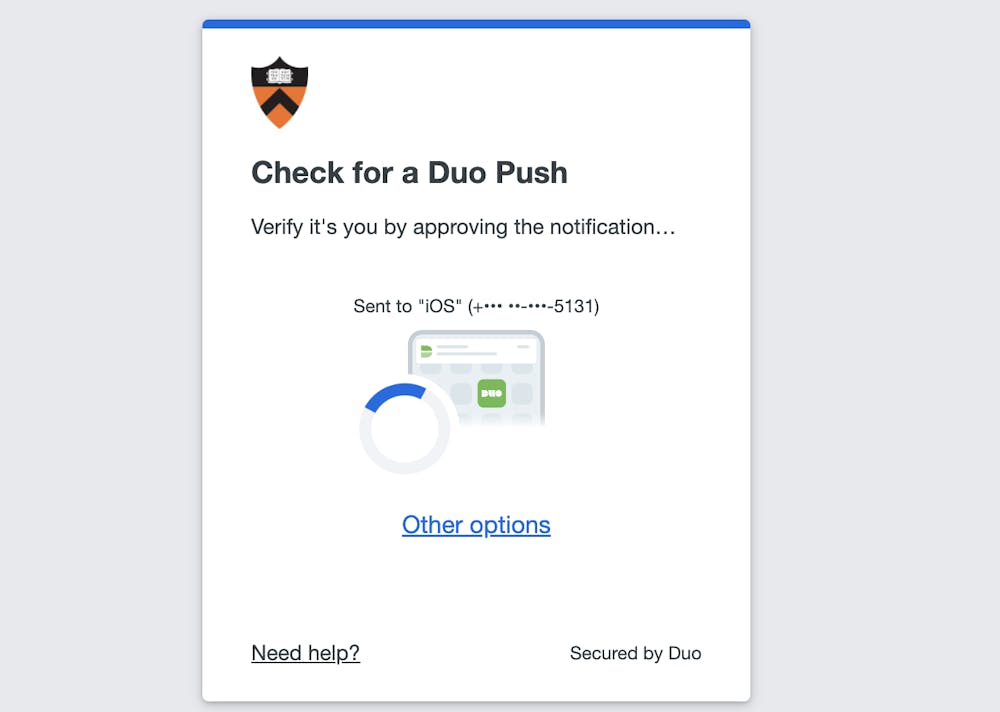
I laughed aloud when reading the recent, clever humor article on an imagined plan to add DUO Mobile, our lovely campus multi-factor authentication (MFA) service, to dorm door locks so as to inconvenience undergraduates as much as possible, all the time. But I also shed a tear at the lampooning of the MFA’s effectiveness and security, which I hold near and dear to my heart. While somewhat annoying, the presence of DUO Mobile does considerably more good than harm by protecting all of our personal information and the University network at large.
The basis of MFA is that you are enhancing the security of a system by requiring multiple “factors” for login. These factors are broadly defined by the federal government’s Cybersecurity and Infrastructure Security Agency (CISA) as something you know (e.g. a password), something you have (e.g. your phone, where you accept DUO push notifications), or a biometric (e.g. a fingerprint). This is to create a failsafe, so if any one factor is compromised, the possible infiltrator is still locked out. And whether it is apparent or not, MFA is one of the most important factors in not only safeguarding your own personal information, but also securing Princeton’s network as a whole.
Before I make the case for MFA as a technology, I want to highlight the gravity of how vulnerable systems can be to rudimentary attacks. Consider as an example the recent string of phishing emails sent to a variety of princeton.edu email addresses over the summer soliciting student research assistants, such as those falsely claiming to be on behalf of Prof. Ryan P. Adams. While the “gmail.com” sender domain and questionable grammar of the message were hopefully obvious indicators of suspicious activity, all it would take is one unsuspecting student to enable this attacker to do harm. Had a student responded to the email requesting more information, the infiltrator could have used a variety of low-cost, highly effective tools for stealing information, such as the publicly available blackeye tool that can make near-perfect malicious spoofs of common login pages in an instant. With stolen credentials in hand, the infiltrator would then have free range to any account that uses them, regardless of platform. From there, this attacker might attempt privilege escalation, using existing access as a stepping stone to further exploitation. This could include moving laterally, infiltrating more sensitive accounts affiliated with your personal information, or vertically, attempting to compromise deeper and more critical systems on the Princeton network.
The case of vertical escalation has particularly concerning consequences for the student body at large. A common nonchalant response to the rigorous security practices on University systems is along the lines of “What’s the worst they could do, steal my course schedule?” While I agree that an attacker having access to your hundreds of listserv emails per day and your Writing Seminar drafts is not the end of the world, this reasoning neglects two central aspects of your student account: it’s association with and storage of important demographic information, such as on TigerHub, and its privileged access to certain University services, including Office of Information Technology (OIT) resources. These avenues are likely the first places an attacker will look to facilitate privilege escalation.
In an attacker’s eyes, you are just the first step towards a broader goal: 82 percent of data breaches in 2021 involved a human element. Of those, 89 percent were in pursuit of some financial motive. In short, attackers generally have a clear (often financial) objective that requires user participation to succeed. Whether they are hunting for your personal financial information, or are seeking to infiltrate Princeton’s network to target its vast financial resources, it is up to you to stand in their way.
The good news is that MFA apps like DUO are the first line of defense in protecting against this barrage of attacks. The prevalence of phishing I have highlighted, along with advances in other password cracking techniques, means using passwords alone (i.e. a single factor) is increasingly insecure. Some would even argue passwords have reached the point of obsolescence. MFA has taken up the mantle as the new minimum standard of security to compensate for human fallibilities: the counterweight to the frightening prevalence of phishing is the ease at which it can be stopped by utilizing one additional factor. At any point in the long, strikingly straightforward chain of events I outlined above, having MFA enabled on your device could stop an attacker in their tracks. Moreover, you would be instantly notified of your credentials being compromised by receiving a push notification when you are not actively logging in — allowing you to instantly change your passwords and mitigate the takeover before it can spread elsewhere.
Another important point to consider when griping midway through your log-in process: we already use multiple systems with MFA in our daily life. Ironically, one of the best examples of effective MFA is the dorm doors at Princeton. They combine something you have (i.e. your prox) with something you know (i.e. your PIN) to prevent easily breaking in if someone were to lose their prox or accidentally divulge their PIN. This system works extremely well — dorm break-ins on properly functioning doors are basically unheard of — and few people resist the need to have both factors.
Has anything I have written changed the fact that rummaging around for your phone when you are trying to expediently login to a system is annoying? No. But the profound security benefits behind mandatory MFA far outweigh the daily minor inconvenience of tapping a few buttons. So in those extra 15 seconds you have to wait to log in, enter a small thank you into the OIT ether and rest easy knowing our network lives another day.

Christopher Lidard is a sophomore from Baltimore, Maryland. A computer science concentrator and tech policy enthusiast, his columns focus on technology issues on campus and at large. He can be reached at clidard[at]princeton[dot]edu.