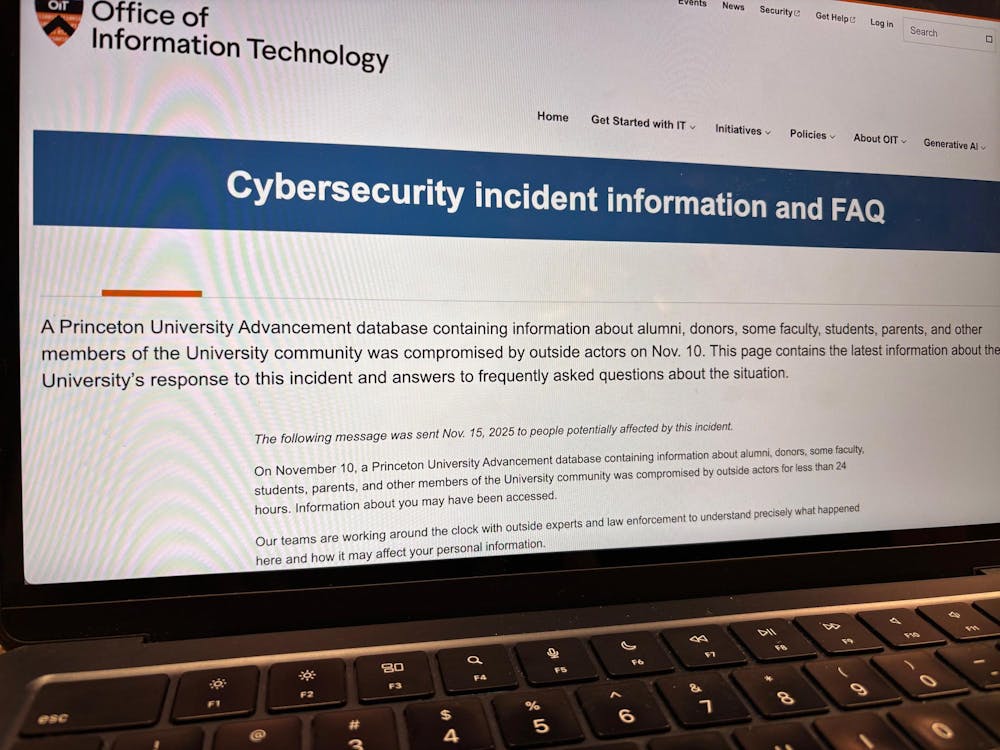
A University Advancement database containing information about alumni, donors, students, parents, some faculty, and other members of the University community was compromised on Nov. 10, putting their data at risk of access by outside actors.
According to a Saturday announcement from the Office of Information Technology (OIT), the breach occurred after outside actors targeted a University employee with access to the database through a phone-based phishing attempt. The incident began on Nov. 10 and was blocked within 24 hours.
The database compromised included names, email addresses, telephone numbers, and home and business addresses, along with information about University fundraising and donations. It “generally” did not include sensitive information like Social Security numbers, passwords, or credit card and bank account numbers.
“[W]e moved as quickly as possible to notify those potentially affected so they can be vigilant for potential phishing attempts,” University spokesperson Michael Hotchkiss wrote in an email to The Daily Princetonian.
Hotchkiss added that “the University, in consultation with outside experts, has worked continuously to understand the incident.” OIT noted in an FAQ page posted after the breach that the investigation is ongoing and may take several weeks.
No suspects have been identified in OIT’s investigation, and officials have not yet determined precisely what information was accessed. OIT notified law enforcement of the incident.
The notification of the breach comes immediately after a widespread disruption that impacted printing and single sign-on, and other OIT resources beginning Friday. About 51 percent of “affected servers and related infrastructure” have been restored as of 5 p.m. on Sunday. Hotchkiss wrote that the service outage was unrelated to the service database.
A much larger-scale attack hit the University of Pennsylvania on Oct. 31. Individuals claiming responsibility released thousands of internal documents online, including donor records, confidential University memos, and personal identifying information for Penn students, alumni, and donors. The group claimed it had accessed data for 1.2 million users, although Penn disputes that claim.

The Penn hackers gained full access to a Penn employee’s account and posted samples of the data on LeakForum after sending mass spam emails to the Penn community. Penn reported the breach to the FBI, and the group has threatened to release or sell additional data.
OIT said they had no information indicating Princeton’s breach was related to that at Penn or “any other incident.”
As the investigation continues, Hotchkiss urged all community members to practice “good digital hygiene” by lengthening and regularly updating passwords for online accounts.
Chief Information Officer Daren Hubbard and Vice President for Advancement Kevin Heaney both warned the University community to “be alert for unusual messages that purport to come from the University. No one from Princeton University should ever call, text, or email you asking for sensitive information such as Social Security numbers, passwords, or bank information.”
“We continue to monitor and improve our security efforts, reinforcing our already robust cybersecurity measures, including continuing to enhance training for all users,” Hotchkiss wrote.
Haeon Lee is a News contributor for the ‘Prince.’ She is from Brooklyn, N.Y. and can be reached at hl1389[at]princeton.edu.
Please send any corrections to corrections[at]dailyprincetonian.com.