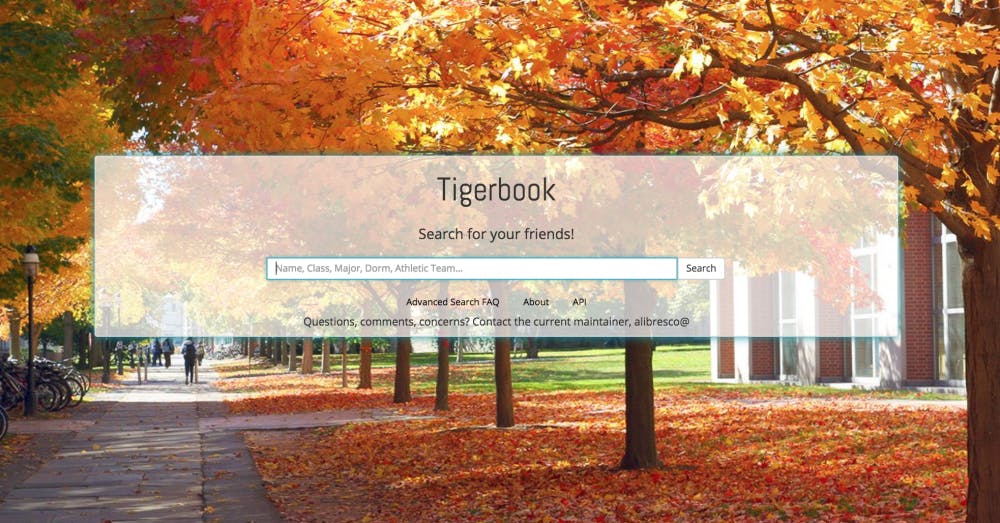
The Undergraduate Student Government Executive Committee alerted the student body in an email on Oct. 15 of their concerns about the confidentiality of a popular student directory application, Tigerbook.
“We have very recently learned that the student(s) tasked to manage and update [Tigerbook] have access to what is being searched and who is making each of these searches,” Undergraduate President Myesha Jemison ’18 wrote on behalf of the committee. “This means that student managers could view individual search histories from Tigerbook that have been recorded according to each student’s netID.”
In light of the email from the USG Executive Committee, University students have expressed concern over their privacy with regards to Tigerbook. However, the managers of the TigerApp system think that the email didn’t illuminate the full picture.
“It’s very easy to frame the email in a negative light, saying that there could be a breach of privacy, and that negative outlook is very present right now,” USG TigerApps Chair Rushy Panchal ’19 said. “We want to make it clear that there is not a breach of confidentiality. Rather... we know there is a set of data being collected.”
“What the press release is actually saying is that USG was not aware that search queries were being stored,” computer science lecturer Jérémie Lumbroso, the faculty advisor for Tigerbook, said in an interview. “Now that they are aware, they want to have a discussion on whether or not it’s a good idea.”
Tigerbook allows students to search for the names, residential college, dorm locations, roommates, and academic concentrations of other students. It is only accessible through the Princeton Central Authentication Service (CAS), meaning that students must supply appropriate netIDs and passwords in order to access the information.
The application was created by Hansen Qian ’16, Rohan Sharma ’14 and Ivo Crnkovic-Rubsamen ’15 as a capstone project for the class COS 333: Advanced Programming Techniques.
Before Tigerbook, student information — such as students’ majors or the residential colleges that they belong to — was scattered across a few platforms for students to access. Only through the University Directory, the Residential College Facebooks, and the Office of the Dean of Undergraduate Students Organization Page could students learn more about their peers. According to Sharma and Qian, the goal of Tigerbook was to consolidate this scattered information.
“We wanted to provide a more user-friendly, feature-filled, and flexible search experience than what the University already had,” Sharma said.
“From the beginning, Tigerbook was meant to be a project built by students, for students, in order to address a gap in the market that [the Office of Information Technology and USG were] unwilling or unable to fill,” Qian said in an email.
After the Tigerbook creators graduated, Lumbroso selected Adam Libresco ’19 to manage the project. Lumbroso would stay on as faculty advisor.
“Tigerbook deals with students’ records, so we felt that it was probably a good idea that I stay involved,” Lumbroso said.
As manager of the application, Libresco worked to establish a functioning Application Programming Interface (API) for Tigerbook.
“The reason why API is a good idea is that every student on campus who wanted to integrate their app in the student system needed to download the information from the Residential College Facebook,” Lumbroso explained.
Under this process, according to Lumbroso, students could download data and keep it to themselves, so there was no tracking mechanism for the data.
“Tigerbook API provides a convenient, robust place for [student creators] to be getting this information,” Lumbroso said.
Along with the initiation of API, Libresco and the computer science department began collecting analytics on individual events.
“The reason we’re [collecting analytics] is that we want general aggregate user statistics for Tigerbook,” Libresco said. “We want to see how many people are using it per day, we want to see how many unique people are using it each day.”
In order to see unique usage, the program recorded the netIDs of students who searched for information.
“We made no attempt to hide that we were doing this. We consulted all relevant University data policies before doing this,” Libresco said.
According to Libresco, this data could be used by Tigerbook to make improvements to the application or to provide evidence and statistics for the University if Tigerbook were to seek funding.
“There’s so much space there and you see tech companies doing it all the time, [looking] at how their apps are being used and then [finding] ways to improve them as a result,” he added.
“We used a program that manages and handles analytics,” said Libresco. “Basically, we send to that program in real time, as it happens, something that says ‘netID A searched netID B.’”
"There are ways you can attempt to anonymize data,” said Libresco. “We looked into them and they didn't seem reasonable for a number of technical reasons."
Another possible use for the analytics was a list of how many times students had been searched, similar to Google Trends.
“All we collect is each individual event, but the data we compiled is a ranked list of students who have been searched and the number of times they’ve been searched,” Libresco said. “Though, we erased all data about who searched them. There’s no names at all on who searched them.”
In order to gather both this list and general statistics, Tigerbook, like all tech companies that gather these statistics, uses an analytics program.
“We configure that analytics program to give us out the information we want,” Libresco said. “And the information we wanted was graphs of usage statistics and a ranked list of how many times people had been searched.”
Libresco, Qian, Lumbroso, and Panchal stressed that this type of data collection is standard usage among tech-industry companies. The University also provides limited standards on whether or not this is allowed for student-run apps.
Sharma, Qian, and Crnkovia-Rubsamen were originally concerned about privacy with the project, even though the student information for the app is collected from sources that were already available to University students or to the public. The group originally met with President Christopher Eisgruber ‘83, who approved their project.
“In the beginning, there were no [University] policies around privacy and confidentiality,” Qian said in an email.
Panchal noted that this lack of privacy guidelines can cause challenges for student app developers, particularly when their projects become popular.
“I don’t think a lot of people go into [COS 333] thinking their apps will be used by so many people,” Panchal said.
Libresco also noted the gaps in the limited data policies that the University has in place.
“It should never be known to anybody who is searching whom, because we think of that as a huge breach of privacy,” said Libresco. “It still doesn’t actually violate any University data policies, but we think of it as a huge breach of privacy.”
OIT has an Information Security Policy which was last updated on Aug. 15, 2017. The information students can find on Tigerbook, such as dorm locations, falls in the Unrestricted Within Princeton (UWP) category.
“University Information is classified as Unrestricted Within Princeton (UWP) if it falls outside the Restricted and Confidential classifications, but is not intended to be freely shared outside the University,” the policy states. “One example is the Faculty Facebook.”
“Facebook and Google have more data collection than we can imagine and their teams have to decide the ethics behind that,” Panchal said. “It’s hard for students.”
“The person managing Tigerbook has access to everything but that’s because they’re running Tigerbook, they’re supposed to have access to everything,” said Lumbroso. “Having server logs is a perfectly normal, typical aspect of a tech service.”
“My position is that the student in question did nothing wrong but instead spent a year and a half of his time doing non-glamorous work for campus infrastructure, and none of this has been mentioned anywhere,” Lumbroso said.
Meanwhile, USG is now taking several measures to ensure the protection of student privacy. In light of the Tigerbook concerns, USG is now investigating the data security access and confidentiality of other TigerApps. USG will also more clearly articulate guidelines and protocols that are available to both developers and student users, placing confidentiality as a primary goal of all current and future TigerApps. Finally, USG will recommend to the University that these guidelines and confidentiality contracts be extended to applications created in COS 333 classes that are CAS-protected.
“We want this to be a learning experience for us and an opportunity to better serve and advocate for students,” Jemison said. “We also want to ensure that confidentiality with regard to student data is a priority in the future and we want to hold ourselves and TigerApps managers accountable to this.”
“A big step of moving forward is improving the resources for students on campus so they can learn more about [privacy and data ethics] considerations,” Panchal said. He further explained that USG will continue a conversation with the COS 333 professor in the next week in order to ensure that professors can provide better information on ethics and privacy so that these considerations can be kept in mind when students are making projects.
“You see two types of reactions from people very familiar with tech and not familiar with tech,” Lumbroso said. “This is not a Tigerbook issue; it’s a privacy issue.”